Dr. Wrong and the Art of Digital Misdirection
In 2008, Satoshi Nakamoto introduced the world to Bitcoin.
In 2016, Craig Wright introduced the world to Craig Wright. Oh, and also claimed to be Satoshi, which implies he owns half a billion dollars in BTC.
You probably already know this is a load of bunk, but I've yet to see a concise article on how Wright managed to trick several news organizations and even Gavin Andresen. We already know how Wright tried to pull a digital magic trick on the whole internet (but again very few easy to understand summaries). I want to explain it as simply as I can[1]. After that, knowing the formula for the online trick, I think it's pretty clear how he managed to pull off his tricks in person.
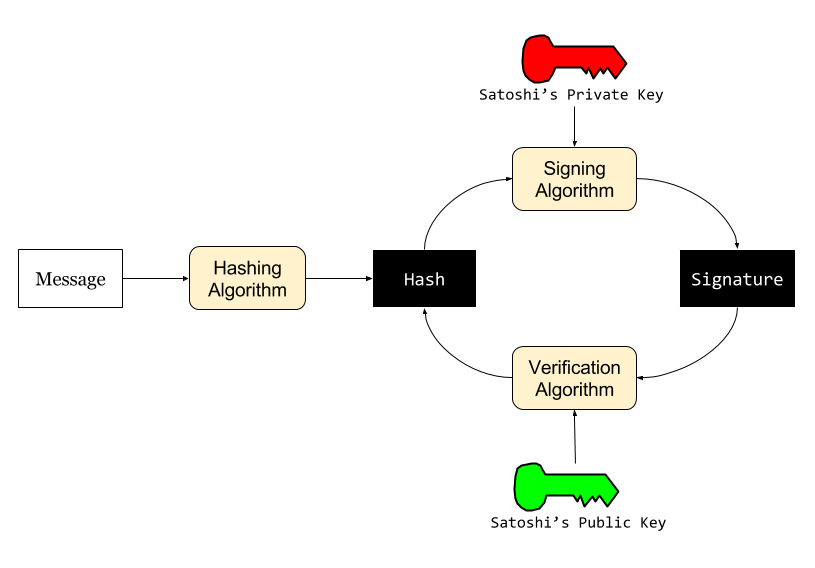
In this blog post, Wright strongly implies that he has multiple private keys that were only known to Satoshi. If so, he probably is Satoshi. To prove it's true, he just has to sign a message as shown above. It's actually simple. Here's how it should go:
- Wright hashes a message[2].
- Wright signs the hash.
- You verify his signature.
Notice that the only part possibly involving human readable text is the Message. The rest of the data will just look like a bunch of meaningless junk to a lay person. And importantly, the hashing algorithm only works in one direction. You can't get the original Message from the Hash.
Getting you to stare at a bunch of meaningless junk is the crux of the trick.
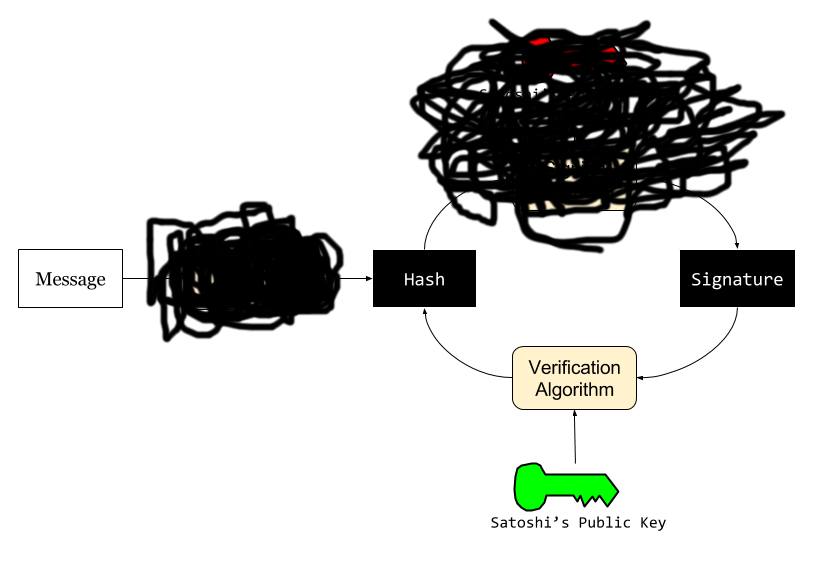
Now, for what actually happened.
- Wright shows you a picture of a message, part of it at least. Maybe it's a letter by a famous author, maybe it's a message of your choosing (pick a card, any card).
- ...
- Wright hands you a hash, which is supposed to correspond to the message. Trust him.
- Wright hands you a signature.
- Wright hands you a public key, which is clearly only associated with Satoshi.
- You verify the signature.
Guess what? The verification works. Don't get confused here. There's nothing broken with the verification algorithm. And Wright doesn't have to tinker with it at all. Some have pointed out that there is a typo (signiture) in some of Wright's scripts. Considering he copied the script from a gist that doesn't contain that error, I think it's possibly a clever misdirection.
What Wright pulled was a replay attack. Meaning he copied/pasted existing, publicly available data (including hash, signature, and key) and then just showed it to you again. It was valid data then and it's still valid now. He copied them from the blockchain, Bitcoin's historical ledger.
Is it a weird coincidence that he found all 3 on the blockchain? No, because digital signatures are a good chunk of what makes Bitcoin possible.

Craig Wright can't actually do the part scribbled out above, the signing. If he had that capability, he could do it in a few minutes from the comfort of his own home. That would settle the matter almost definitively, but he can't and won't.
Witnessing this and still thinking that Wright is Satoshi is like catching God in the act of faking his own miracles. If that doesn't make sense to you, welcome to the club.
Now, how does Wright trick someone sitting in the same room? Someone technical. Someone like Gavin Andresen?

I have to say first that I'm very sympathetic towards Gavin. If you listen to what he's saying, you can clearly tell that he's probably more desperate to meet Satoshi Nakamoto than anyone else on the planet. Think about that for a minute. Think about what it would be like to form your career and your identity around an invention, to have only exchanged a few technical notes with the inventor, to worry about whether they're even alive for years, and then finally to get the chance to meet them face to face. To shake their hand!
I hope that hand you're shaking isn't the hand of a skilled conman. Suffice it to say, there's some baggage here. Read Gavin's post on the meeting (emphasis mine):
Part of that time was spent on a careful cryptographic verification of messages signed with keys that only Satoshi should possess. But even before I witnessed the keys signed and then verified on a clean computer that could not have been tampered with, I was reasonably certain I was sitting next to the Father of Bitcoin.
It was a mistake to agree to publish my post before I saw his- I assumed his post would simply be a signed message anybody could easily verify. And it was probably a mistake to even start to play the Find Satoshi game, but I DO feel grateful to Satoshi.
So here's what we know for sure (assuming Gavin Andresen is being truthful, which I don't doubt):
- Andresen is flown to London to meet Wright and associates
- Andresen brings his own USB stick
- Andresen supplies a message shown below
- Wright appends something to the message (possibly important!)
- Wright has his own computer
- Wright demonstrates a "signing" associated with Satoshi's keys
- Wright also supplies a "factory sealed" computer for verification purposes
If you followed along earlier, you know what's coming. On his own computer, Wright can demonstrate whatever sort of fakery he wants. He can type any series of commands into a terminal and get exactly what he wants.
For their test, Andresen chose the message "Gavin's favorite number is eleven." Wright added his initials, "CSW," and signed the message on his own computer.
He can appear to be "hashing" Andresen's message and instead outputting a predetermined hash. The original message is irrelevant.
Likewise, he can then type commands that appear to be digitally signing Andresen's message and are actually just outputting a signature.
That's just his own machine though. The next step, where Andresen verifies the signature, is the real mystery. But I don't think you have to grant Wright supervillain powers to understand how it could be done. There's no need to hack the wifi or perform some MITM attack.
I think there are three possibilities in decreasing order of likelihood:
1. The hashing was done on Wright's machine and copied to Gavin's USB stick
A mistake, but an understandable one considering Gavin was already convinced and certainly not expecting this kind of replay attack. The verification seemed like the important part, after all, not the hashing.
2. A hashing utility was compromised on the "fresh" laptop
First, understand that even if the fresh laptop really was "factory sealed" that means nothing.
Wright could have been shipped a Windows laptop with an image that replaced a built-in hashing utility like CertUtil. This is slightly more far fetched, but not at all difficult for a wealthy businessman.
3. The laptop somehow opened a compromised version of Electrum
I find this really hard to believe for several reasons. But there is an interesting point.
At first, the Electrum software's verification of the signature mysteriously failed. But then Andresen noticed that they'd accidentally left off Wright's initials from the message they were testing, and checked again: The signature was valid.[3]
Another clever misdirection? Maybe! But if I'm going to wildly speculate, I'm gonna go big.
If Electrum was compromised, Wright would need a way to get verification to fail on junk messages in case Gavin tried to get it to fail intentionally. You wouldn't want Electrum just saying OK VERIFIED on every input. But if it was simply waiting to see the letters CSW, Wright was able to get Electrum to both fail and succeed at the appropriate times without knowing what message Andresen would choose. Yes, it's Andresen who spots the error, but he's a talented programmer looking at a short string. Who wouldn't?
Option 1 or 2 seem the most likely, but I'm aware that Andresen could dispute those claims easily (I emailed him, but I don't expect a response). If it was something like #3, we'll never know.
Bamboozled
You might argue that the offline trick could be totally different from the online one. True, but why waste a good magic trick?
In recent sessions, I have used a total of 10 private keys are associated with bitcoin addresses. These were loaded into Electrum, an SPV wallet. In one of the exercises, I signed messages that I will not detail on this post for a number of individuals. These were not messages that I personally selected, but rather ones that other people had selected. In some instances, we ensure the integrity of the process by downloading a new version of the electrum program, installing it on a fresh laptop that has just been unboxed having been purchased that afternoon and validating the signed messages on the new machine.
The version of electrum that I run is on Centos Linux v7 and runs via Python. For the exercise I noted above we used Windows 7 and Windows 10 on different occurrences.
That strongly implies to me the demos are nearly the same, only with a few necessary details changed. You can even see him happily describing which operating systems he has tested his trick on. Amazing!
The sniff test
Many will say that the only thing that matters in this situation is math. Move coins or GTFO. Sign with genesis block or GTFO.
I agree, but I would also pay attention to what Wright is saying and doing. What if we hadn't figured this particular trick out? I will argue that we already had plenty of evidence suggesting Wright was a fraud:
- Wright tried to edit old blogposts to suggest he was involved in bitcoin (God faking his own miracles again)
- Wright has lied about his degrees
- Wright makes fundamental errors describing the core algorithms in Bitcoin
Just look at his attitude. Satoshi spent years in hiding (and practically disappeared from all communication in 2011). Wright says he wants to be left alone and gives interview after demo after interview. Going to conferences and subtly hinting that you invented Bitcoin is not an attempt to hide.
What's amazing to me is that many folks are convinced just on the basis of Wright being vaguely connected to Bitcoin since around 2014 or Wright giving a few winks and smiles in 2015. FFS, people. I was mining in 2011. I actually do have a Masters degree in computer science. That doesn't make me Satoshi. If that "evidence" is convincing anyone, well, it's no wonder that religions only a few decades old can be so sacrosanct...
It was obvious to me that Dorian Nakamoto was just a confused, old man.
It's obvious now that Craig Wright is just a confidence man. You don't need math for that, but it doesn't hurt either.
Vote on HNDiscuss on Hacker News, you know, if that's like your thing.
Hitherto
Time Travel Is ******* HardYear in Review 2015
Turning 10 bucks into $1600 - How I gambled against a dotcom millionaire and won
Permalinks
Short: http://jere.in/16Pretty: http://jere.in/dr-wrong-and-the-art-of-digital-misdirection